Contents:
Introduction
Somewhere in 2020, I watched the documentary about online privacy and social media on Netflix about how social networking and big tech giants are making money at the cost of psychological manipulation and constant tracking of their ‘users’.
How to ensure online privacy in an era of growing invasiveness?
The technology that connects us also control us
The Social Dilemma.
In November 2019, I had a chance to attend a conference in New Delhi regarding the Challenges of Cyber Crime and Cyber Security, which touched upon the issues of online privacy and good cyber hygiene practices. Sometime later, I read ’Digital Minimalism’ by Cal Newport, which further touched upon the issues and widened my horizons.

Somewhere in 2020, I watched the documentary about online privacy and social media on Netflix about how social networking and big tech giants are making money at the cost of psychological manipulation and constant tracking of their ‘users’. After that, I started reading extensively about some of the best practices related to privacy, tried to implement many of them and had varying experiences with them.
In the past year, I have tried to educate, tell people and share what I know about the dark side of the internet and social media. Most of them felt alarmed at the seriousness of the situation and reciprocated the concern. So finally, I decided to share what I know about the topic so that an average internet user may better appreciate the problems and implement better solutions.
Web Interaction
The Problem
Privacy means differently to different people, and a universal definition for it doesn’t exist. It’s an abstract concept; Oxford English Dictionary defines it as,
the state of being alone and not watched or disturbed by other people or the state of being free from the public’s attention.
by extension of the above definition, online privacy means the state of being alone while online or using the internet or protection from undue intrusion while working online.
How is the personal online space of individuals being challenged with disregard to privacy?
To delve deeper, we first need to understand a cookie and a tracker, which are so widespread in online/web browsing that the chances are you must have already come across these terms by now. So let’s get ourselves on the same page with our understanding of these terms.
Web Cookies are a set of information stored locally on your browser, which can be specific to some programs and can store some basic information like your name, e-mail etc. The purpose of it is to improve the user experience by ‘remembering’ some essential things. To understand better, let’s take the example of online shopping, most of us have used some websites for online shopping. The process is simple; we browse the online shop, add some products to our virtual cart, and then pay. Have you ever thought that if you somehow close the page and move to some other page to make comparisons or check prices there and then return to your page by reopening it, the products are still in the cart? Shouldn’t they be gone when you close the page? Well, it’s a web cookie in action for you. The same goes with watching online videos; you frequently log in to YouTube and watch videos online. You find yourself still logged in when you return some other time on your YouTube page. That’s your YouTube cookie storing information for you.
But they seem to be improving the user experience. Won’t It be pretty inconvenient to repeatedly add such basic information; what’s the harm in storing such basic information?

Before answering that let’s also understand the concept of trackers. They are programs designed to collect, store and share user information about their online activities. Let’s take the example of Netflix, which actively tracks user activity on its app to recommend shows of interest to the user. Similarly, you must have come across YouTube recommended videos based on the real-time usage tracking of your activity on YouTube.
Some advertising algorithms and cookies, known as tracker cookies, target user behaviour across the internet and multiple apps. Facebook is known for delivering user-specific ads and tracking user behaviour over the internet. This is the reason for those ubiquitous ads we start seeing all over after any product search on our device. These ads harm privacy because they collect vast amounts of personal data patterns and data points to deliver optimum and targeted ads customised to our specific queries. Sometimes it seems magical, but actually, it’s pretty creepy and if used irresponsibly it invades online privacy.
The Custom Search engine.

I remember when I first told a friend of mine about the variation in google search results from person to person for the same search query and his utter disbelief in grasping the concept. The issue is so understated and unknown to normal net users that the trailer for ‘the social dilemma’ begins on this note where Tristan Harris, former design ethicist at Google and co-founder of Centre for Humane Technologies, explains,
‘that’s not by accident, that’s a design technique.’
Tristan Harris
As an average internet user, getting the same content for the same search parameters (of course, by same search string we don’t mean searching coffee shops near me as that search string is geo-location specific) should be a fundamental right. Furthermore, the search engine shouldn’t actively profile user behaviour per query. But most of the common search engines, including all the big ones by ‘design technique’, actively profile their users even when they are not logged in and serving content they deem suitable to the user. This choice should rest with the user to decide which content to consume for a given search parameter, not with some search engine algorithm.
The all reading e-mail.
How many times it has happened that after we make a reservation for a flight online, the tickets/booking are delivered in our mailbox (personal experience with Gmail) and suddenly auto-populated in our calendar. Ever wondered how does that happen? Of course, the company is reading our emails to ‘optimise’ services for the users by giving them more convenience by auto-populating their appointments and calendars. Without access to our e-mails and direct invasion on our online privacy, such a service is not possible.
What’s the harm in sharing information over social media?

The question is not about sharing of information but about the extent of sharing. With so much of our data online, most social hackers don’t even need top-notch coding skills to exploit our online vulnerabilities. Simple social information shared online may do the trick. Most of my friends ask what possible harm can publicly shared birthdays, and family information do? Well, the short answer is pretty much. It depends on who has access to the information and what they do out of it. This video which I came across around three years back, changed my perspective about sharing personal information on social media. It has been an eye-opener to all the people I have shared it with. Please have a look at the link.
Isn’t it creepy? How easily a social hacker can manipulate the very people, who are supposed to keep our information secure into handing over the data. Just think about it; what happens if somehow we lose access to our login credentials of any service? Usually, the service provider asks for information like phone number, e-mail address, date of birth, spouse or mother’s maiden name etc., to confirm our identity and hand over the data. But we have voluntarily displayed this information online to anyone looking at it. Maybe it’s time to review our social media profiles?
Take Back the control?
Now we have understood the first part of the problem, the solution is pretty simple, i.e., to minimise our online presence and interact with the web as per our needs and choices. In the conference I attended on cyber security, one of the speakers said the most straightforward solution was to use a simple phone without any internet connection, no pen drives in our systems and a strict firewall with a minimum net interface.

But in this era of continuous connectivity, it is not practically feasible to almost negate our online presence, so some suggestions to ensure cyber hygiene which I have personally practised are as follows:-
- Before trying out this suggestion, check your present security levels via this online tool. Find an excellent privacy-centric web browser to interact with the web over all your devices. There are many options freely available online. Depending on your preference and requirement, you can find an optimum browser online. The basics that we are looking at are their capability to prevent trackers and cookies and minimise our browser fingerprint online.
- Find an excellent private search engine that’s not profiling you for every keystroke. Many private search engines are based on the data from google search but provide you anonymity while using.
- Find a good e-mail service which is not making money reading your mails. This transition probably looks the most challenging thinking how much we are synced in the existing ecosystem, but believe me, it is just a psychological barrier. Once you cross it, there’s no looking back.
- Minimise your social media presence. The best is to eliminate or delete any personal accounts. There are other more intimate and personal ways to keep in contact with our near and dear ones.
We’ve moved away from a tools based technology environment, to an addiction and manipulation used technology environment. Social media isn’t a tool waiting to be used. It has its own goals, and it has its own means of pursuing them by using your psychology against you.
Tristan Harris, former design ethicist at Google and co-founder of Centre for Humane Technologies.
VPN – Do you need it?
In most of my discussions with friends and family, the initial response to VPN is negative. Somehow, it’s attributed to the shady work most hackers do with VPN use, and people respond by saying that we have nothing to hide. It’s like assuming all dark web is inherently wrong because it’s “dark”! To be clear, any non-indexed part of the web (which doesn’t appear in search engines) is the dark web, so it has all shades of the good, the bad, and the ugly.
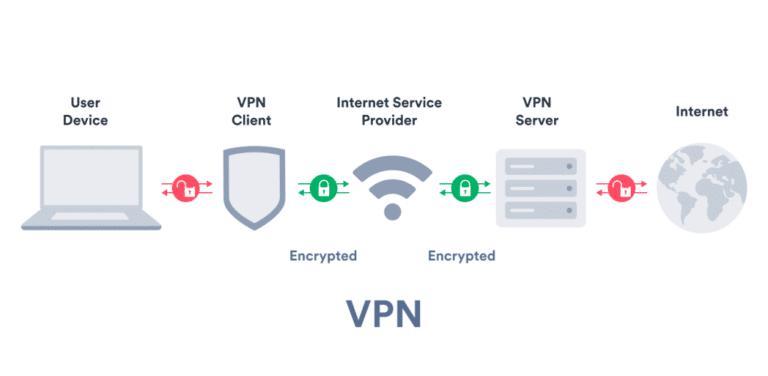
Coming back to the issue, VPN basically lets you connect via your network/service provider to a private network, which connects you to your ending node/address. The instant benefit is that to your service provider, it seems that your traffic is routed to the VPN server, which in turn reroutes to your final destination. It hides your browsing patterns and IP address over the internet. To anyone checking your IP after you connect to the VPN server, any tracking attempt for an IP address will show the IP address of the VPN server. How much can an IP address reveal about you? You can check it via this tool.
If you decide to use VPN, then avoid free one’s; as the old saying goes, ‘there are no free lunches’ a free VPN will compromise your security and do you more harm than good. There are many VPN service providers which you can find according to your budget and need to ensure optimum online privacy for your needs.
That’s ok, but do you need VPN?
In my personal opinion, it depends upon what you expect out of your VPN service. Do you need it? You need to be clear about your reasons for getting one.
Consider this scenario, you’re one of the 1.5-2 million people living in a big city, and your internet service provider is providing service to thousands of customers in the town. Of course, they can see your online activity and patterns, but so what? (Coming back to the argument, I’m not doing anything illegal.)
Now consider yourself as an online influencer, a prominent journalist, a top bureaucrat, some leading politician or some key decision-maker in any organisation that you work for. Now for your internet service provider, the incentive to monitor you is incredibly high. You are not just one among the thousands on whom they may waste time and energy monitoring. But you are a crucial influencer of your field; they will undoubtedly be interested in knowing your daily habits. Still, you are not doing something illegal, but they can make out patterns of your routines by watching your browsing patterns which are far more worth now.
And then, of course, you can access perfectly legal online content which is geo-blocked by bypassing it via VPN.
IS VPN use legal?
Usage of VPNs is completely legal in India. There are no legal restrictions regarding VPN usage in India.
What about the promises made by the leading VPN companies?
Some myths that need to be busted here are:-
- VPN usage increases online security by making your connection more secure. – all those claims about military-grade security are not wrong but exaggerated. Modern sites and web-browsers already use HTTPS encryption, which they call ‘military grade’ or AES encryption. Even this blog is HTTPS encryption providing you’ military grade’ encryption every time you visit it.
- Without VPN, your ISP can look into your data when you’re visiting websites – as I said before, that’s not happening till the time you’re on HTTPS. All your service provider can look into is the target site you’re visiting. ISP doesn’t have direct access to your activity on the target site, as the communications between you and the target site are made in HTTPS encryption.
- VPN usage makes you completely anonymous online – Online; no one is entirely anonymous. With right skills and adequate resources, anyone can be tracked. If someone is trying to hack into ISRO or DRDO servers using a VPN, they will be living in a fool’s paradise to assume that they won’t be tracked down.
VPN’s are good at masking your IP’s and blocking you out from mass surveillance(algorithm-based) being done online to ensure your online privacy. Your ISP’s don’t get direct reads on you, and you can anonymously surf over the web. But, if someone needs to specifically target you, as I said before, with adequate resources, a skilled hacker can track anyone.
The Password Manager
If you’re to change a single habit that can cause tremendous amplification of your online privacy and security, I would recommend generating and storing good, solid and uncrackable passwords.
Before we move further, first check using this tool if your password has ever been exposed online. If yes, then check the service which exposed it.
A list of the top 100 passwords that people use will throw some light on how seriously most of us take our online security. If your passwords happen to be on this list, some significant introspection is required for your password generation. Without further ado, Let’s delve into the practice of generating good passwords:-
Make up some good random memory marker know only to you.
What’s that supposed to mean?
Let’s assume that I have a lovely dog whom I got on the 15th of August 2014, at someplace called Dak Pathar, and his name is Besan.
So from this information, let’s generate a unique memory marker known exclusively to me as:- i got Besan on 15/08/14 at Dak Pathar and now for my password, let’s select:- igBo15-08/14@DP
As you can see to some random person, this password looks unconnected and incredibly complex and good luck to any of the hackers trying to brute force through that! That’s how we can generate using mnemonic techniques extremely complex passwords. (BTW, I do love dogs and have three of them, but none of the other facts has any resemblance to my real life, so don’t start with the above password against my accounts.)
And Another lousy practice which I, by no exaggeration, can claim that more than 90% are guilty of(until two years ago, I was also doing things the same way) is keeping the same passwords for our several online accounts.
But what’s the harm in it?
Well, the harm is apparent. If one of our accounts is compromised, all of our accounts are compromised as simple as that.
So what to do?
For best cyber hygiene practices keep unique passwords for all your services. NEVER EVER REPEAT A PASSWORD!
But I have some thirty online services requiring passwords; I can’t generate enough complex mnemonic markers and remember them for all the services that I use.
The Password Manager

That’s where passwords managers come into play. You only need to generate an incredibly complex master password for your password manager, and the password manager will take care of the rest; well, that’s the job of it. By using Passwords Managers, you generate incredibly complex passwords for all your services, and all of them are unique. That’s the beauty of it. They are incredibly useful tools to ensure cyber hygiene and online privacy.
But can we trust the password manager with our passwords?
By design, the working of a password manager doesn’t store your master password in the password manager. To open a password manager vault, it needs two sets of keys; one is a master key and another some secret key(or whatever name your service provider gives it) generated locally on the device. Only the end-user knows both these sets of keys. The provided link explains in great detail the working of password managers. Please go through it if you want to understand its functioning in detail. In short, you’re in a much better shape with password managers than without them.
There’s a whole lot of cloud-based password managers available in the market, do your research and pick anyone from the list; you can thank me later for it. For me, it’s the most fantastic piece of technology I invested in and works like a charm, and maintains my security on all my devices.
Online Privacy and hygiene checklist
- [ ] Privacy Centric Web Browser
- [ ] Privacy centric Private search engine
- [ ] Private email service
- [ ] Decreasing your social media footprint
- [ ] VPN (only if you need)?
- [ ] A Good Password Manager
I use all of them, including a VPN. Those interested in the specific services that I use can connect to me personally regarding my suggestions.
The Battle is far from over
Whatever I have shared here took me a lot of time to learn. The process involved unlearning the wrong habits and changing the way I interact with the web. For the past two years, I have not been on any social media channels and have tried to develop and adopt some reasonable practices to follow while online. I have been attempting to educate people about the safe practices to adopt while using the web, cyber hygiene, online privacy and warn them of the shortcomings. This article condenses my learning and experiences and provides some valuable tools to appreciate the issue’s gravity better. There is no ‘one-fits-all approach; it’s all about a trade-off that we are comfortable in. And to those still wondering when most of the web is free for access, what’s the product?

It’s the gradual, slight, imperceptible change in your own behaviour and perception that is the product.
Jaron Lainer, founding father of Virtual Reality Computer Scientist




The section on online privacy hygiene is critical. Regularly updating passwords and being mindful of the information we share online is the first step towards safeguarding our digital footprint.
Maybe if we start sending boring emails, they’ll stop reading them out of sheer boredom. Worth a try?
I never knew emails could read all our stuff. that’s kinda scary, don’t u think? makes u wonder who else might be watching.
Imagine if there was a spell to protect our online privacy. Would definitely be easier than remembering all these passwords and using VPNs.
All this talk about password managers, but what if they get hacked? Then what? It’s like putting all your eggs in one basket.
Honestly, not sure if anything can truly ensure our privacy online anymore. It feels like a lost cause with how advanced tracking has gotten.
While the points about VPN legality and usage are valid, it’s imperative to discuss the ethical implications of circumventing geolocked content. Where should we draw the line?
Actually, the legality of VPN usage for such purposes greatly varies by country and can indeed pose ethical dilemmas. It’s a grey area in many jurisdictions.
This article is such an eye-opener! Never knew about the dangers of sharing too much on social media. Definitely thinking twice before posting now.
i think the part where u mentioned custom search engines is really important. its like people forget they track everything. not just ads but everything.
hey Vishal, interesting take on the online privacy. but, the vpn part got me thinking, does using a vpn slow down the internet speed? been curious about that.
I’m new to all this. Can someone explain how a password manager works in simple terms? Keep reading about them but still a bit confused.
yo, so is there like, a best vpn for gaming? latency is a killer, don’t wanna mess with my ping lol.
Loved the section on taking back control. It’s empowering to know that while the internet has its dark sides, we’re not entirely helpless. Tools like VPNs and password managers are indeed lifesavers.
Fascinating read. It’s akin to the age-old debate of freedom vs. security. In stark historical contexts, societies have often sacrificed one for the semblance of the other. Online privacy seems to be the modern arena for this trade-off. One wonders, at what point does the scale tip too far?
does using a vpn make the internet slower? asking for my cat, he’s got no patience for slow videos.
As a parent, this security talk is worrying. How do I ensure my kids are safe online? Any specific tools or settings you’d recommend, Vishal?
The part on custom search engines is intriguing. However, isn’t it more about trading privacy for convenience? We’ve somewhat consented to this by using free services. Not saying it’s right, but it’s a two-way street.
About sharing stuff on social media, isn’t it all about how we use it? like, a bit of common sense goes a long way, right? But yeah, those settings can be a maze.
great piece on online privacy, Vishal. Always thought VPNs were a tad overrated, but seeing how you’ve put it, makes sense to have one these days.
hey, interesting article. just wondering how these password managers actually keep our stuff safe? read somewhere they can be hacked too, kinda makes you think twice, doesn’t it?
yeah, heard the same. feels like jumping from the pan into the fire. what’s even the point if it adds another risk?
Actually, most reputable password managers encrypt your data, making them highly secure. It’s about choosing the right one and using it smartly.
Interesting points about VPN legality. It’s crucial to remember that while VPNs can provide security, they’re not a free pass to bypass laws or regulations. Always check the legal standpoint in your country.
Ah, the eternal battle for online privacy. Here we are, trying to shield ourselves from the prying eyes of the digital world with our VPNs and password managers. Makes you wonder, who’s watching the watchers, right?
yo, this article’s got me wondering, does using a VPN affect gaming ping or speed? always thought that might slow things down.
This take back control section is legit what I needed. Didn’t even know half these things could potentially breach my privacy online. Thanks Vishal, it’s a step in the right direction.
Yes, Kiran! The first step to protecting your online privacy is awareness. Vishal’s doing a great service by shedding light on these critical issues.
Honestly, feels like all these privacy measures are just making things more complicated than solving anything. Every other day, there’s a new thing to worry about. Can’t we just use the internet without being paranoid 24/7?
Reading through the privacy pointers, it occurred to me how little we’re educating our kids about these issues. They’re growing up in this digital era without knowing how to safeguard their online presence. Time to change that.
The part about custom search engines caught my eye. It’s fascinating and a bit frightening to think about how customized our web experiences have become. It’s all crafted to keep us engaged and coming back for more.
About the social media info sharing, sometimes, it’s not just about harm but about comfort too. Knowing what’s being shared and what’s not makes a huge diff. Not everything is a privacy invasion, right? Or am I missing something here?
Can anyone explain that bits about password managers? like, how safe are they really? Having one thing remember all my passwords seems risky, lol.
Just read about VPNs n how it keeps our online stuff safe. Got me thinking, maybe it’s time to get one? Always thought it’s kinda techie stuff beyond my grasp. Cheers Vishal for breaking it down easy. Gotta keep our data safe, right?
Absolutely, Ravi! VPNs can be a game-changer in protecting your online footprint. And it’s really not that complicated, plenty of user-friendly options out there. Check out some reviews; you’ll find the right fit.
But do VPNs really keep all that data safe? Heard some stories about them keeping logs and stuff.
Through personal experiences and reflections, the review highlights the importance of understanding cyber hygiene practices in navigating the digital landscape.
Thanks!! 😊